In the world of ad marketing, where every click and view counts, a new threat has emerged that's causing headaches for digital advertisers and publishers: SDK spoofing. This sneaky technique messes with the data that shows how well ads are working. Imagine fake clicks and made-up views, all designed to make ad campaigns look successful when they're not. It's like a shadow that's hard to see, but it's messing up the game.
The severity of the issue can be well described through a statistic that states that SDK spoofing is capable of siphoning off 80% of all ad budgets. This blog dives into what SDK spoofing is all about, how it works, and most importantly, how digital advertisers and publishers can shield their campaigns from its harmful effects. Let's shed some light on this shadowy issue and find ways to outsmart it.
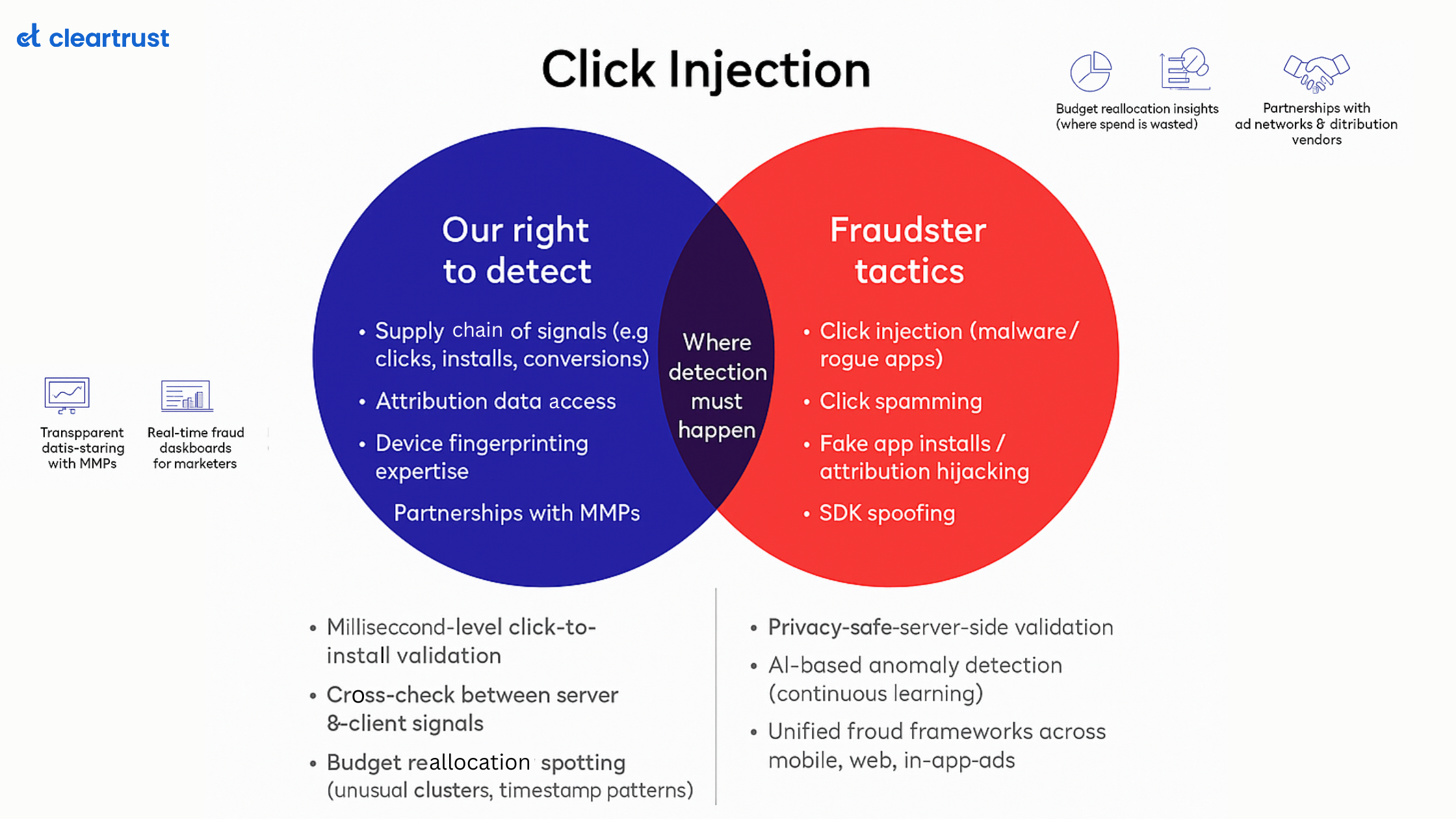
What is SDK Spoofing?
SDK spoofing is a cyber maneuver in which fraudsters manipulate software development kits (SDKs) to fake genuine app interactions. This technique involves tactics through which fraudsters fake an app install using a legitimate device though there is no install that happens in the first place.
The stages of this process involve the following-
- Falsified Installation Reports : Fraudsters mimic legitimate installations by altering data sent to attribution systems, causing them to register fake installations.
- Simulated User Interactions : Bogus interactions, such as clicks and ad views, are simulated by imitating the communication between apps and SDKs.
- Fabricated In-App Actions: Fraudulent SDKs mimic in-app activities, leading to seemingly authentic user engagements that never actually transpired.
- Data Falsification: Fraudulent data packets are crafted to mislead analytics platforms, making the fraudulent activity appear genuine.
- Conversion Deception: False conversions are reported, leading advertisers to believe they've achieved their desired outcomes, when, in fact, no real conversion occurred.

How does it impact advertisers?
- Distorted performance metrics- DK spoofing creates a false sense of success by fabricating engagement metrics like clicks, views, and conversions. Advertisers rely on these metrics to gauge the effectiveness of their campaigns and make informed decisions. With inflated numbers caused by spoofed interactions, advertisers might allocate more budget to underperforming channels, believing they are generating high engagement. This not only wastes resources but also undermines strategic planning.
- Budget Misallocation and Wasted Resources- When advertisers invest in campaigns based on fraudulent engagement data, they unknowingly funnel funds into channels that don't truly deliver value. This budget misallocation can lead to underwhelming returns on investment (ROI) and diminished overall campaign effectiveness.
- Erosion of Trust and Reputation- In the competitive digital landscape, trust is paramount. Advertisers build relationships with audiences based on the perceived authenticity of their campaigns. SDK spoofing, however, tarnishes this trust by presenting false engagement data. When users don't engage as the inflated metrics suggest, it can lead to a disconnect between the advertised experience and reality. This disconnect erodes user trust and damages the reputation of both advertisers and publishers.
How to avoid SDK Spoofing?
- Vet your partners carefully-Partnering with reputable ad networks, publishers, and attribution platforms that maintain stringent security measures can help you tackle this threat at the foundation level. It is important to conduct thorough due diligence to ensure that their commitment to fraud prevention aligns with yours.
- Implement Multi-Layered Verification- Another proven technique of countering SDK spoofing is to employ a multi-layered verification system that scrutinizes user interactions and conversion data from various angles. Combining device fingerprinting, IP analysis, and behavioral patterns to unveil inconsistencies can prove effective.
- Regular Audits and Reviews- Various patterns in traffic engagements and impressions can be monitored to counter this threat. Routinely audit your traffic sources and review engagement patterns. Looking for sudden spikes in engagement or unusual conversion rates that could indicate the presence of SDK spoofing will assist in effective decision-making.
- Utilize Anti-Fraud Solutions- The best way to ensure that all the strategies are well executed through a single audit system is by leveraging advanced anti-fraud solutions. These solutions, like those from ClearTrust, employ machine learning algorithms to detect anomalies and aberrations in user behaviour. These solutions can swiftly identify and neutralize instances of SDK spoofing.
As we traverse the intricate landscape of mobile ad marketing, SDK spoofing is a stark reminder of the ever-evolving challenges that digital advertisers and publishers face. By staying vigilant, vetting partners, implementing robust verification systems, and embracing cutting-edge anti-fraud solutions, the ad marketing ecosystem can emerge stronger, more resilient, and fraud-free.