From ad stacking to install frauds, the mobile advertising ecosystem has witnessed numerous challenges. The rapidly advancing technology has not kept fraudsters out of this race as they continue employing complex techniques to disturb, disrupt and infect mobile ad campaigns.
While there are multiple techniques for committing such fraud, these are largely based on attribution hijacking or fake installs. Attribution hijacking involves real users engaging with the ads but unknowingly generating attributes or impressions which are credited to the fraudsters illegitimately. Fake installs, on the other hand, involve fraudsters faking installs and impressions and impersonating real users using multiple devices through click farms or any similar means.
Let us discuss the various types of mobile ad fraud.
Types of mobile ad frauds
1. Ad Stacking
One of the most known techniques of committing ad fraud, involves multiple ads being stacked upon one another. While the user is engaging only with the ad placed on top, multiple advertisers end up being billed due to the ads stacked together with the ad on top. Thus, per user, the fraudster may get benefitted numerous times and the user may not even be aware of the fact that they are being tricked.
While identifying an ad stack is not a cakewalk, one metric that can raise the curtain from this hoax is the time stamp in which the engagement is reported on a single ad placement.
2. Attribution fraud
Attribution fraud involves taking fake credits for an app install. Fraudsters use malware that keeps track of users’ activity once it is installed on their devices. The moment a user installs an app, the malware tracks the ad campaigns relevant to the app installed and generates a fake click report by attributing the user’s engagement click to its name. As a result, the last click for an app install from such a campaign is credited to the fraudster who gets paid for the organic install without any effort,
3. Click farms
An offline version of ad fraud can be seen through click farms. These are physical locations from where mobile ad frauds are committed using a swarm of mobile devices, cheap labourers and click farmers who are employed for the sole purpose of generating fake impressions on mobile ad campaigns.
From faking impressions to app installs, click farms escape vigilance by changing IP addresses through VPNs and hiding their activities behind magnetic features available through various Android and iOS devices.
4. Click spamming
As the name suggests, this technique involves generating fake clicks in the name of users who have not engaged with the ads at all. This can be done through a fraudulent app that presents impressions as clicks through fraudulent reports and claims a share of the advertiser’s budget. IVT management solutions like ClearTrust offers filters and solutions to tackle click spamming and block traffic from sources that initiate such clicks.
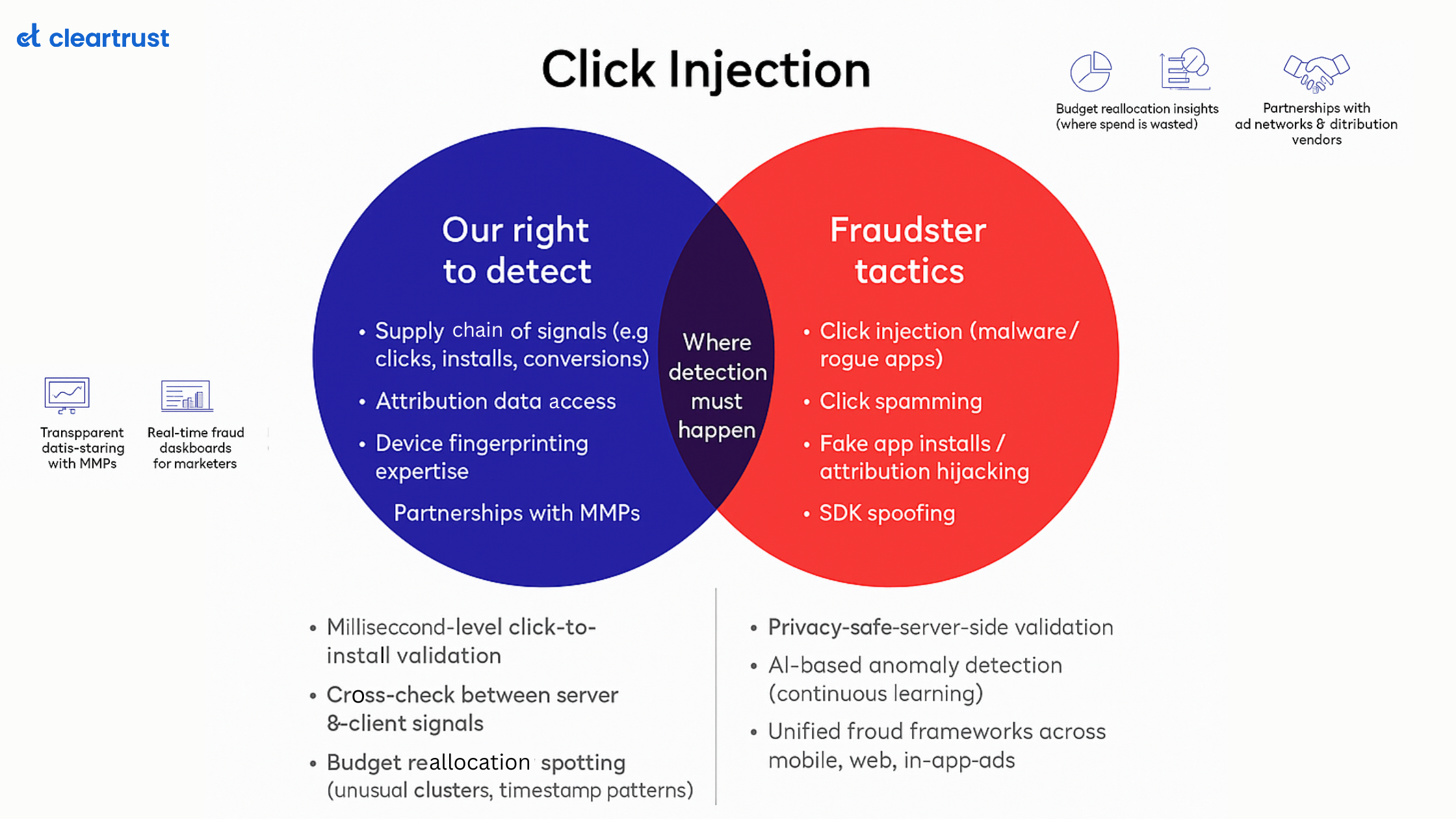
5. Click injection
Click injection involves a fraudster hijacking the app install of real users by listening to the install broadcasts. Once an installation happens, the click triggering the installation will be charged to the fraudster even before the installation is completed. The install broadcast informs a fraudster about an app installed in the user’s device through a junk app which is lying dormant in the user’s device.
6. Device ID reset fraud
This method arises out of a drawback of both the Android and iOS operating systems. These allow users to reset their device IDs which, when successfully executed, will signal any app installs and re-installs as originating from a new user. This, in turn, led to the bad actors capitalizing on this opportunity.
A seemingly small number of devices can be used to carry out this fraud. Once an app is installed and enough engagements have been undertaken from the same, the fraudsters reset the device ID of the phone before re-installing the app. As a result, every illegitimate install will also appear as an organic one only because it’s originating from a unique device ID.
7. Bundle ID spoofing
Under this technique, the fraudster misrepresents the ads being run on one app. The advertisers may believe that their ads are running on a specific app while they might be running on another app. This happens when the fraudster assigns fake identifiers to the second app thereby creating a bundle of IDs that impersonates legitimate apps where ads are meant to be shown.
8. SDK spoofing
SDK stands for Software Development Kit. This is a highly sophisticated scheme wherein a malware-infused legitimate app is used to generate clicks and impressions for a different app without the latter being installed. This means that a fraudster can create an app and without marketing the same or having it installed in the user’s device, the app can attract engagements and impressions from another app.
9. Emulated devices
Emulated devices are simulations of mobile devices and operating systems on computers and similar devices. These are usually used to test an app on multiple devices without the need to physically possess different devices. However, the problem arises when fraudsters use this to generate fake impressions and engagements on in-app ad campaigns by creating fake users.
Since there is no genuine or real user engaging with the ads or taking action, the advertiser’s marketing budget is exhausted in the hands of the fraudster.
10. Click redirection
This technique is more common on the mobile web. When a user visits a page to view some content, he/she might be redirected to a page asking him/her to install an app even though the click was not meant to be on an ad or so. There is a fake script triggered that redirects the user to the install landing page. In case the user ends up downloading the app as a result of such a redirection, the fraudster shall be attributed for the conversion.