Server-Side Ad Insertion (SSAI) fraud is one of the largest threats to the CTV ecosystem as it enables the fraudster to skip detection to a great extent. While fraudsters are constantly deploying SDK spoofing and device spoofing to generate invalid impressions, an advanced version occurs when they use spoofed information to send invalid ad requests to the ad server.
Commonly used in OTT/CTV advertising, SSAI has slowly gained traction due to its similarity with traditional advertisements where ads travel in line with the video content being streamed embedded in the form of a package. However, the two can be differentiated on the grounds that the traditional ads occur at the device level while SSAI at the server level.
Let us understand SSAI in detail and how is it exploited by fraudsters
What is SSAI?
SSAI or ad stitching is an ad delivery technique in which the ad is stitched and delivered with video content. In CTV, while the content is being streamed through the Content Delivery Network (CDN), publishers send ad requests to an ad insertion server. This server passes these requests on to an ad server that supplies the ad content to the insertion server. On receiving the ad, the insertion server stitches the ad to the video content being streamed and sends it to the CDN which delivers the ad to the user.
In SSAI, the video stream and ads are determined in advance rather than the bid requests being sent and served in a fraction of a second. Moreover, the ad insertion server supplies both the ad content and the video content to the CDN together unlike traditional advertising wherein the video content is obtained from the CDN server. In contrast, the ad is obtained from a separate third-party server.
What does an SSAI fraud look like?
For committing any type of fraud, the fraudsters always target the end user and play around with their interaction with the ad content. SSAI fraud is no different. Remember how we spoke about spoofing device information earlier in this blog? In a similar manner, the fraudsters take advantage of the entire user activity being open to the SSAI proxy server that composes HTTP browser requests.
There can be fake proxies used by fraudsters to send spoofed HTTP header requests by faking all the HTTP header fields.
The entire sequence of events is as follows-
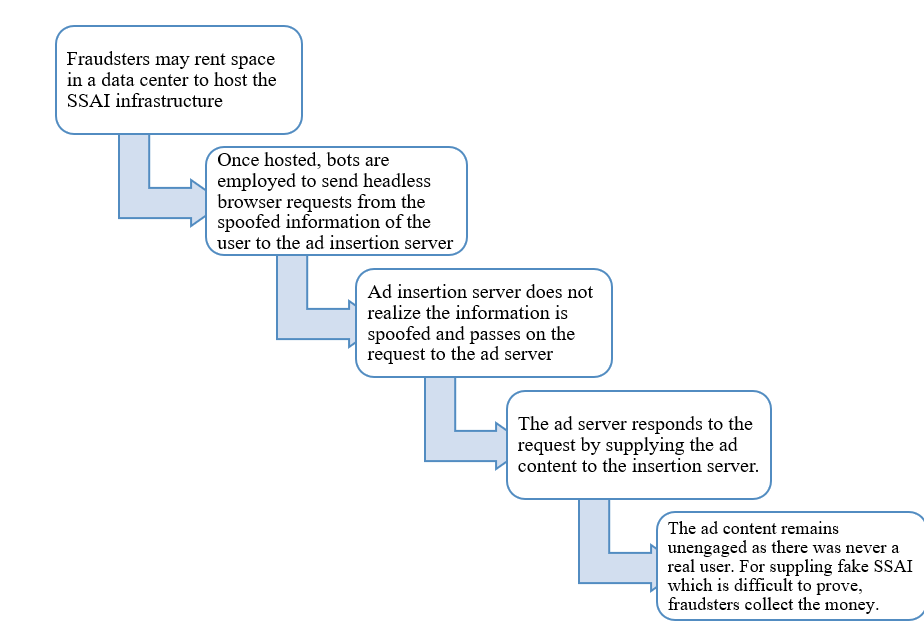
SSAI is more susceptible to fraud due to the whitelisting of SSAI IPs/servers which is done to avoid false positives in ad fraud designations by the supply chain partners. It is important to be noted that a technique that was developed to overcome monetization challenges for publishers and avoid ad blockers has now turned into an attractive option for scammers to conduct frauds.